Cognito, IAM Identity Center
Cognito
AWS Cognito is a web and mobile app authentication, authorization, and user management service. With it, users can sign in using a username and password or a third-party service like Azure AD, Amazon, or Google. AWS Cognito has two main components;
- the User pools, a user directory that allows users to sign in, and
- the Identity pools, which give users access to other AWS services.
The User pools and Identity pools can be used independently or jointly.
Allowing unauthenticated guest access to your application using Amazon Cognito
You can use Amazon Cognito authentication as an alternative to directly using AWS Identity and Access Management (IAM) with both frontend SDKs and direct HTTPS requests.
You may want to use this form of authentication for the following reasons:
- Unauthenticated users - If you have a website with anonymous users, you can use Amazon Cognito identity pools.
- Your own authentication - If you would like to use your own authentication process, or combine multiple authentication methods, you can use Amazon Cognito Federated Identities. For more information, see Getting Started with Federated Identities in the Amazon Cognito Developer Guide.
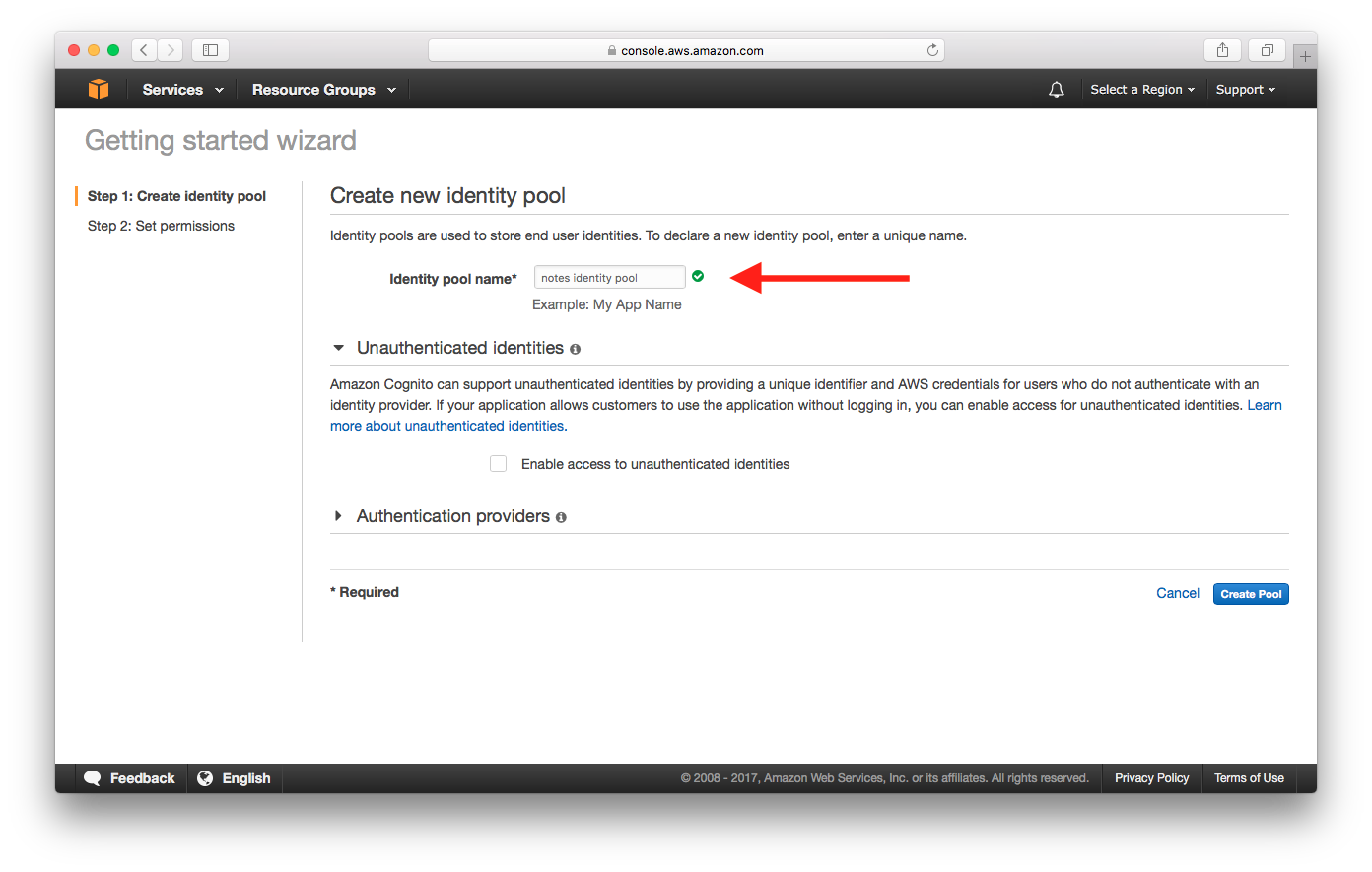
To enable unauthenticated identities in identity pool in console, go to identity pool in the aws console and click on edit identity pool. Now scroll down to unauthenticated identities and enable it. Unauthenticated Identities permissions. Now you can
- make unauthenticated calls using cognito sdk
- if you don't provide credentials, you will be given credentials for the unauthenticated role.
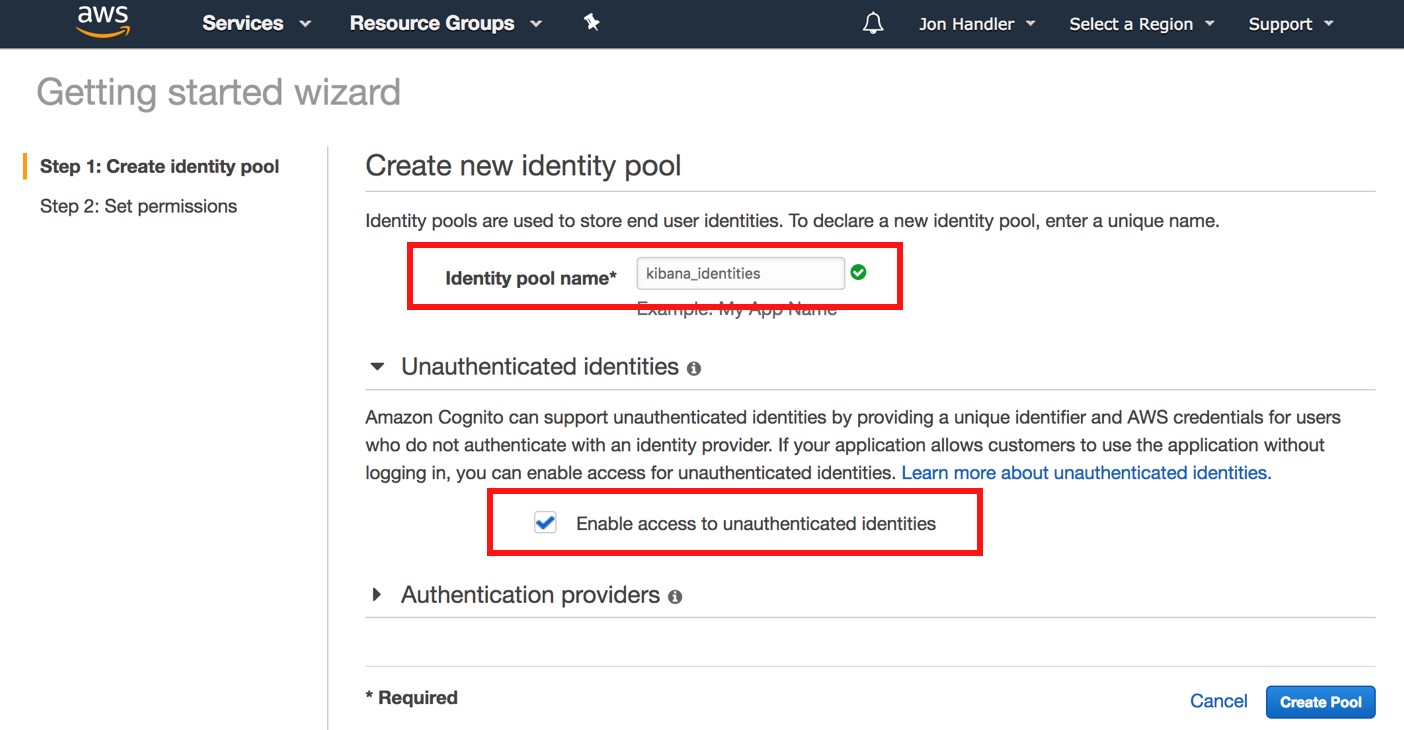
Source: Get started with Amazon Elasticsearch Service: Use Amazon Cognito for Kibana access control
Integrate with Azure AD
- Azure AD will act as an identity provider (IdP), and AWS Cognito will act as a service provider (SP).
- This is for authentication to use credentails from idP to login
An example of SAML identity provider (IDP) is a self-hosted** Active Directory Federation Services (ADFS)** server. ADFS is a service provided by Microsoft to provide login using existing Active Directory credentials.
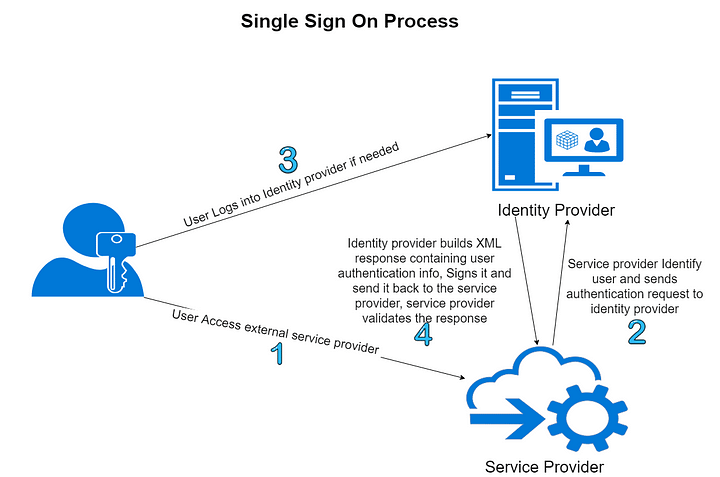
Source: Double Octopus
Azure AD is a cloud-based identity and access management (IAM) solution for enterprises. You can think of it as the backbone of the Office 365 system, which syncs with on-premise Active Directory and provides OAuth authentication to other cloud-based applications.
Before granting the user access to AWS services, AWS Cognito verifies the user's rights with the identity provider while Azure AD checks user identification (e.g., emails, passwords) and asserts to AWS Cognito that the user should have access and that the user's identity if it is legitimate. Check the offical idP authentication flow document to understand how to integrate SAML-based IdPs directly from your user pool.
Reference: Single Sign-On (SSO) using AWS Cognito and Azure AD
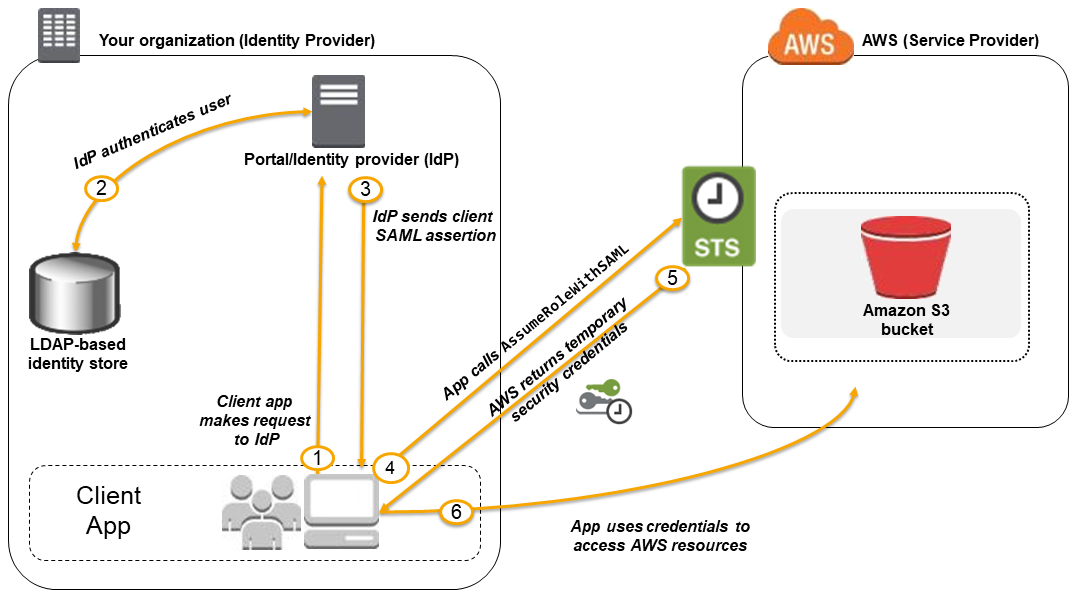 Example: A solution that incorporates an IAM Identity Center single sign-on access from your corporate AD or LDAP directory and also restricts access of each individual user to a designated user folder in an S3 bucket.
Example: A solution that incorporates an IAM Identity Center single sign-on access from your corporate AD or LDAP directory and also restricts access of each individual user to a designated user folder in an S3 bucket.
Cognito User Pools vs Identity Pools
- Cognito User Pools (for authentication = identity verification):
- Database of users for your web and mobile application
- Allows to federate logins through Public Social, OIDC, SAML...
- Can customize the hosted UI for authentication (including the logo)
- Has triggers with AWS Lambda during the authentication flow
- Cognito Identity Pools (for authorization = access control):
- Obtain AWS credentials for your users
- Users can login through Public Social, OIDC, SAML & Cognito User Pools
- Users can be unauthenticated (guests)
- Users are mapped to IAM roles & policies, can leverage policy variables
Summery: CUP + CIP = manage user / password + access AWS services
Custom Login URL
Your AWS account can have only one alias. If you create a new alias for your AWS account, the new alias overwrites the previous alias. The URL containing the previous alias stops working. Also, the account alias must be unique across all AWS products and must contain only lowercase letters, digits, and hyphens.
The AWS account root user and AWS IAM users in the account sign in using a web URL. If you want the URL for your IAM users to contain your company name (or another easy-to-remember identifier) instead of the AWS account ID, you can create an account alias.
The sign-in page URL for your account's IAM users has the following format, by default:
https://123456789123.signin.aws.amazon.com/console/
If you create an AWS account alias for your AWS account ID, the IAM user sign-in page URL looks like the following example:
https://tutorialsdojo.signin.aws.amazon.com/console/
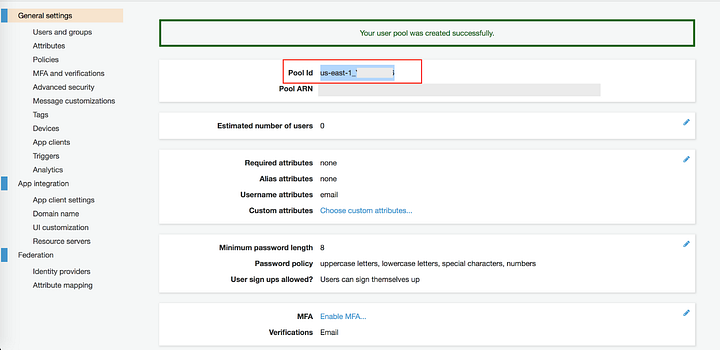
IAM Identity Center (successor to AWS Single Sign-On)
AWS IAM Identity Center helps you securely create or connect your workforce identities and manage their access centrally across AWS accounts and applications. IAM Identity Center is the recommended approach for workforce authentication and authorization on AWS for organizations of any size and type. Using IAM Identity Center, you can create and manage user identities in AWS, or connect your existing identity source, including Microsoft Active Directory, Okta, Ping Identity, JumpCloud, Google Workspace, and Azure Active Directory (Azure AD).
Credential report
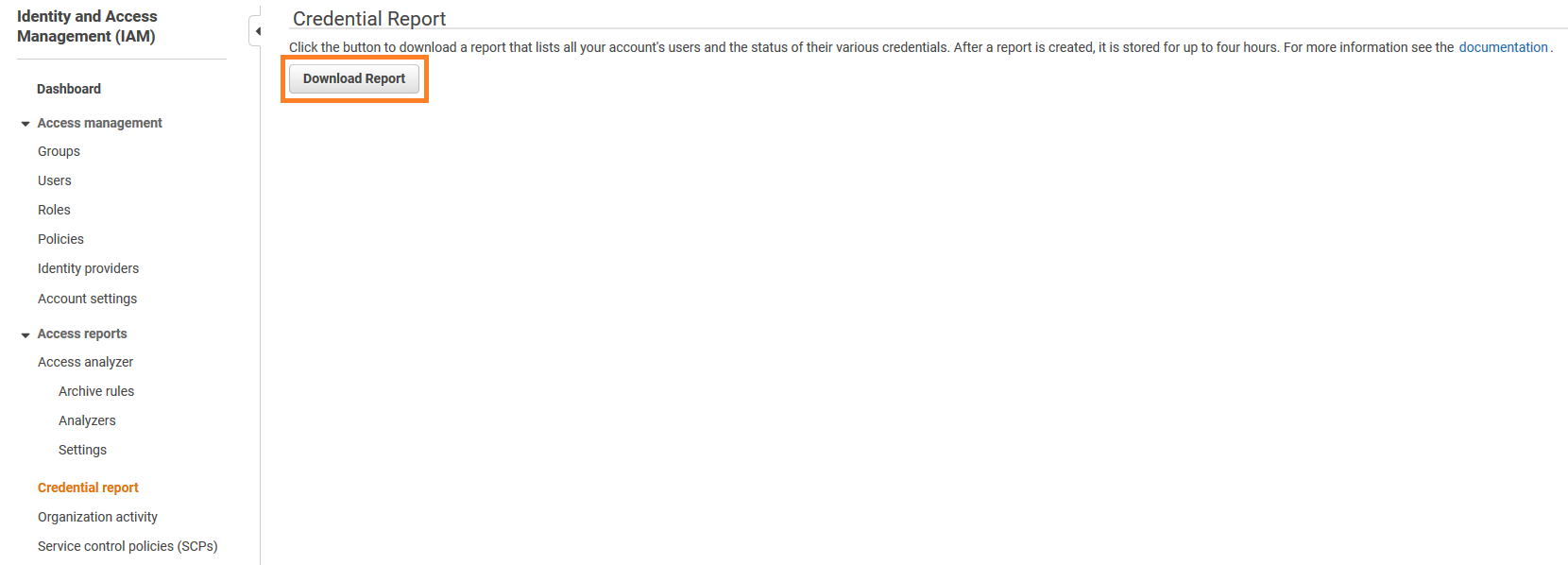
You can generate and download a credential report that lists all users in your account and the status of their various credentials, including passwords, access keys, and MFA devices. You can get this credential report from the AWS Management Console, the AWS SDKs and Command Line Tools, or the IAM API.
AWS SSO
Please check AWS IAM Identity Center as the successor to AWS SSO
A permission set is a collection of administrator-defined policies that AWS SSO uses to determine a user’s effective permissions to access a given AWS account. Permission sets can contain either AWS-managed policies or custom policies that are stored in AWS SSO.
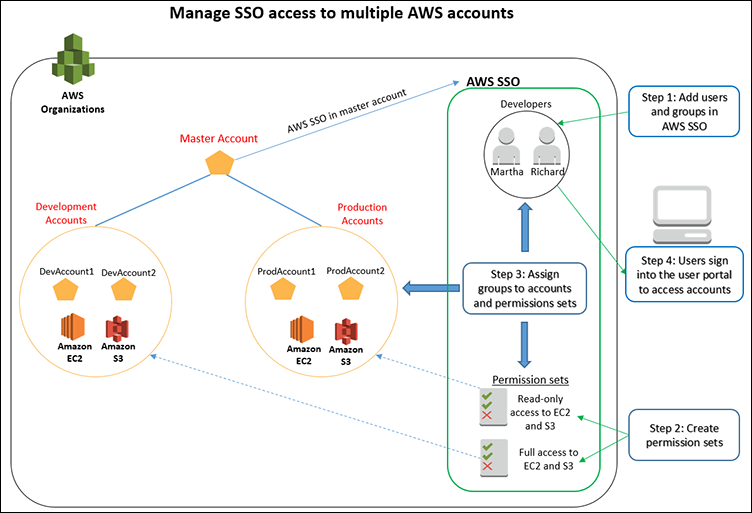
AWS SSO manages access to all your AWS Organizations accounts, AWS SSO-integrated applications, and other business applications that support the Security Assertion Markup Language (SAML) 2.0 standard. This allows you to assign and manage your employees’ access to multiple AWS accounts, SAML-enabled cloud applications (such as Salesforce, Microsoft 365, and Box), and custom-built in-house applications, all from a central place.
AWS SSO automatically provides you with a store by default, which you can use to manage your users and groups within AWS SSO.
- If you choose to store them in AWS SSO, create your users and groups and assign their level of access to your AWS accounts and applications.
- Alternatively, you can choose to connect to Your External Identity Provider using Azure Active Directory or connect to your Microsoft AD Directory using AWS Directory Service.
IAM Identity Center configurable AD sync
This is for provisioning users and groups from Active Directory
IAM Identity Center configurable AD sync enables you to explicitly configure the identities in Microsoft Active Directory that are automatically synchronized into IAM Identity Center and control the synchronization process. Document: IAM Identity Center configurable AD sync